We use an environment protection model developed over the past 20 years which is our 5 Pillars Best Practice framework. This model scales from the smallest system to enterprise and is effectively a way of evaluating clients systems to tease out the risk points.
The 5 Pillar model consists of:
- IT Strategy
- System Security
- Home For Your Data
- Data Recovery
- Housekeeping
Point 2 is around System Security, part of which is End Point Security – For this we use a suite of tools from Trend Micro. Trend has just been named by the Gartner Group as the top player in their respected magic quadrant – Leaders and Visionary.
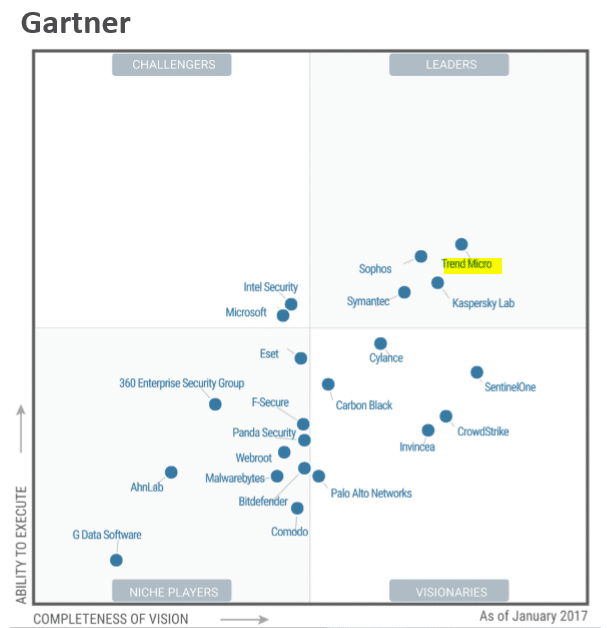
This essentially means they are the best of the best and offer the most superior end point protection available today. If you have suffered from a Virus, Malware or Ransomware, you may be well place to step up your end point security.
In addition they very high scores from NSS Breach Detection Tests helping to comfort you a little more.

We use an environment protection model developed over the past 20 years which is our 5 Pillars Best Practice framework. This model scales from the smallest system to enterprise and is effectively a way of evaluating clients systems to tease out the risk points
If you need help with evaluating the end point protection system that is right for you, feel free to call us on (08) 9441 6300 or Contact Us
Whilst this technology is as good as it gets, the weakest link remains you (or your people).
For this you need education. I am passionate about helping people avoid issues and regardless of if you are a client or not, you need the Security Tips and Tricks to help you stay out of trouble. You can sign up free below:
These Security Tips and Tricks will keep you up to date on the latest crazy happenings in the land of Internet Security around viruses, malware and phishing. Being armed with the right knowledge will help avoid scams and trickery that is rife in our connected world. Be informed, stay safe.

